New Delhi: Ransomware is a type of malicious software that encrypts the data on a victim’s system and demands a ransom for its decryption. If the ransom is not paid, the attackers may threaten to delete or leak the data on the dark web. Ransomware attacks have become more frequent and sophisticated in recent years, affecting various sectors and organizations worldwide.
One of the latest ransomware threats is Akira, which targets both Windows and Linux-based systems. According to the Indian Computer Emergency Response Team (CERT-In), Akira is a ransomware operation that first steals information from its victims then encrypts their data, and conducts a double extortion scheme to force the victims into paying the ransom. In case the victims do not pay, the group releases their data on their dark web blog.
How does Akira work?
Akira uses common tools such as AnyDesk, WinRAR, and PCHunter to facilitate its intrusions. These tools are often present in victims’ systems, and their misuse can go unnoticed. The ransomware group also gains access to victim environments via VPN services, particularly where multi-factor authentication has not been enabled.
Once inside the system, Akira erases Windows Shadow Volume Copies, which are backups of files and folders that can be used to restore data in case of corruption or deletion. This makes data recovery more difficult. Then, it encrypts files with specific extensions, such as .docx, .xlsx, .pdf, .jpg, .png, etc., and adds a ‘.akira’ extension to each encrypted file’s name. For example, a file named ‘report.docx’ would become ‘report.docx.akira’ after encryption.
During the encryption phase, Akira employs the Windows Restart Manager API to terminate active Windows services. This prevents any interference with the encryption process4. After encryption, Akira drops a ransom note named ‘akira_readme.txt’ on the victim’s desktop. The ransom note contains instructions on how to contact the attackers via email or Telegram and how to pay the ransom in Bitcoin or Monero. The note also warns the victims not to rename or modify the encrypted files or use any third-party decryption tools.
How to stay safe from Akira?
Ransomware attacks can cause significant damage and distress to individuals and organizations. Therefore, it is essential to take preventive measures to protect your systems and data from Akira and other ransomware threats. Here are some tips to follow:
- Maintain offline backups of your critical data and ensure that these backups are regularly updated. Offline backups are not connected to the internet or your network, so they cannot be affected by ransomware.
- Update your operating system and applications regularly to fix any security vulnerabilities that could be exploited by ransomware. Consider using ‘virtual patching’ for legacy systems that cannot be updated easily.
- Implement strong password policies and enable multi-factor authentication (MFA) for your online accounts and services. MFA adds an extra layer of security by requiring a second factor of verification, such as a code sent to your phone or email, in addition to your password.
- Avoid clicking on suspicious links or attachments in emails or messages from unknown sources. These could be phishing attempts to trick you into downloading malware or revealing your personal information.
- Use reliable antivirus software and firewall on your system and keep them updated. Scan your system regularly for any malware infections and remove them as soon as possible.
- Educate yourself and your employees about the latest ransomware threats and how to recognize them. Awareness is key to preventing ransomware attacks.
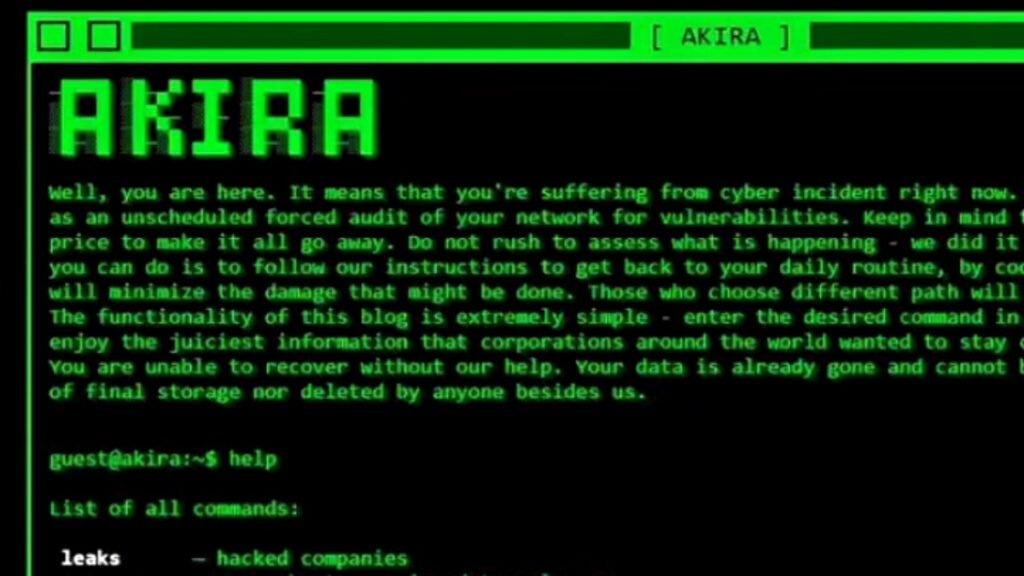
Ransomware Akira is a new and dangerous threat that can affect both Windows and Linux users. By following these safety measures, you can reduce the risk of becoming a victim of Akira or any other ransomware attack.